AirTightening the Bolts on Insecure Networks
By CWNP On 07/12/2010 - 45 Comments
WIPS vendors tell us all about the problems of ad hoc networks and the dangers of hackers, but perhaps they should remind us of the dangers of ad hoc networks and Russian spies. You may have read in recent news that the FBI detained several individuals who were suspected of being Russian spies. During the investigation, some telling evidence was collected by means of Wi-Fi sniffing. As it turns out, one of the suspects would set up shop with a laptop in a coffee shop. Another suspect would drive by in a van, transferring files with the person in the coffee shop via an ad hoc network with “amateurish” security. The FBI caught onto this and was able to sniff the traffic and recover the data. If only the Russian spies had heard marketing messages from WIPS vendors explaining that ad hoc networks are bad. Apparently they’re bad for everyone, spies included.
Speaking of WIPS vendors, the whole point of this blog is actually to make a few comments about AirTight. I’m sure you know the AirTight name by now, but if you don’t, they’re one of the three (previously) third-party WIPS vendors (all named AirSomething). AirDefense was acquired by Motorola, and AirMagnet was acquired by Fluke. Of course, Fluke is not an infrastructure vendor, so their WIPS platform is still third-party; but it seems that their focus lately has been heavily slanted towards Fluke’s primary product lines, which are targeted towards network analysis, and not so much towards WIPS. From all that I see and hear, AirTight is capitalizing on this market opportunity as a small(er) and flexible vendor by partnering and integrating with infrastructure and analysis vendors to extend their appeal to more customers.
Some of the features in their latest firmware upgrades (Spectraguard v6.0/1) highlight their thought leadership, which is certainly on the cutting edge. If you don’t remember, reread some of Gopinath KN’s articles on our blog. He’s AirTight’s Director of Engineering, and a very skilled security researcher.
Anyway, back to the AirTight products. They’ve introduced some excellent new features lately to help differentiate them from the AirSomething crowd; hopefully there’s value to our readers when we highlight the latest and greatest from leading vendors, so that’s what I’m here to do.
Let’s start with a quick WIPS primer, which is only necessary because I want to show you a visual aid that was in an AirTight presentation. In a nutshell, a WIPS serves to automate the monitoring, reporting, and response to security and performance policies. On the security side, the essence of WIPS functionality looks like the graphic below.
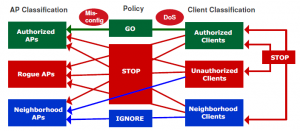
Cool graphic, huh? It simplifies the whole concept of WIPS, as this picture speaks thousands of words.
To optimize their solution’s capabilities, here is a snapshot of what AirTight has been up to:
• One of the key problems with deploying WIPS systems is that you must classify every device as either friendly or rogue, neighbor or local, or, potentially, unknown. If you improperly categorize devices, you run several risks (legal, security, performance, bad neighbor). And, you have to manually classify new devices on a regular basis. And, you have to classify client devices, which can be overwhelming, especially with smartphones and tablets, which will continue to increase, as evidenced by Cisco’s recent announcement of Cius. All this goes to establish that manual classification can be a real pain in the glutes; with proper deployment and configuration on the wired side, AirTight can automate the classification process with several different techniques. One of which is by using their patented wireless-to-wired or wired-to-wireless broadcast marker packets to determine if a device is on the local network. Finding out whether a potential rogue is on the wired network is an important first step to classification. It also helps to identify the risk factor of potential network threats. AirTight alleviates this task with automation.
• Third-party WIPS vendors (both of them) have the unique strength of being able to function as an overlay to any WLAN infrastructure. Third-party WIPS vendors have the unique challenge of having to function as an overlay to all WLAN infrastructures. Let’s focus on that second sentence because some vendors (like Meru) have some pretty challenging proprietary functionality that can really screw with an overlay WIPS system. Meru’s proprietary Virtual Port and Virtual Cell modes are intriguing, but imagine what an ESS-wide BSSID or a per-client BSSID will do to a WIPS and expected WIPS functionality. Truth be told, if WIPS vendors don’t implement proprietary mechanisms to understand a Meru environment, the WIPS solution will be completely ineffectual. That’s exactly why AirTight has been working hard to understand the Meru environment and then incorporate that understanding into its solution. With v6.1, AirTight includes capabilities to detect and accurately report the details of both Virtual Cell and Virtual Port Meru deployments. AirTight’s Meru-specific reporting includes details like the number of physical APs, client-to-AP associations, and more; identifying this information accurately depends upon proprietary information from Meru. In other words, such intelligence would be impossible without assistance from Meru. If you’re a Meru shop and you want overlay WIPS security, make sure your vendor can make sense of Meru’s secret sauce. AirTight can.
• As WLANs are increasingly used for mission-critical applications, the deployment, maintenance, and troubleshooting of those networks will continue to increase in sophistication (and probably automation). You’ll continue to see tighter integration between infrastructure/WIPS vendors and packet/spectrum analysis vendors so that APs and WIPS sensors can be used for analysis of the L1 and L2 environment. To serve the need at the L2 protocol level, AirTight integrates code from the open-source Wireshark platform. Also, they partner with Omnipeek and integrate their solution as well. So, an AirTight WIPS sensor can be used for remote wireless packet captures and analysis. This is great for detailed troubleshooting, and it alleviates the problem of rolling trucks. I’m sure we’ll see more like this from other vendors as well.
Those were three of the big ticket capabilities that stood out for me. Reporting features and processes were fine-tuned and forensic analysis was also improved. While those are important, they’re not nearly as exciting to talk about, so if you care, ask an AirTight engineer. Security has been a big topic lately with the Wi-Fi Alliance’s recent announcements about WEP and WPA, and I’m excited to see if and how this impacts the WIPS market.
Tagged with: AirTight, WIPS, Wi-Fi Security
Blog Disclaimer: The opinions expressed within these blog posts are solely the author’s and do not reflect the opinions and beliefs of the Certitrek, CWNP or its affiliates.




0 Responses to AirTightening the Bolts on Insecure Networks
Subscribe by EmailThere are no comments yet.
<< prev - comments page 1 of 1 - next >>
Leave a Reply
Please login or sign-up to add your comment.