What Is a Switch, Router, Gateway, Subnet, Firewall & DMZ? (Guest Blog)
By Suraj Rojanala On 04/05/2022
Just getting started in networking, this blog post provides a brief and introductory overview of a switch, router, gateway, subnet, firewall, and demilitarized zone (DMZ). These common components and concepts exist in nearly all modern networks.
Switch:
A network switch (also called switching hub, bridging hub, and, by the IEEE, MAC bridge) is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device.
Packet switching allows data to be sent over the telecommunications network in short bursts or "packets" that contain sequence numbers so that they can be reassembled at the destination.
A network switch is a multiport network bridge that uses MAC addresses to forward data at the data link layer (layer 2) of the OSI model. Some switches can also forward data at the network layer (layer 3) by additionally incorporating routing functionality. Such switches are commonly known as layer-3 switches or multilayer switches.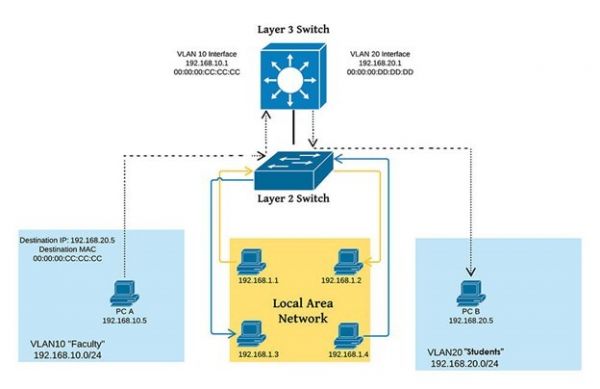
Switches are key building blocks for any network. They connect multiple devices, such as computers, wireless access points, printers, and servers, on the same network within a building or campus. A switch enables connected devices to share information and talk to each other.
ROUTER:
While switches allow different devices on a network to communicate, routers allow different networks to communicate.
A router is a device that connects two or more packet-switched networks or subnetworks. It serves two primary functions: managing traffic between these networks by forwarding data packets to their intended IP addresses and allowing multiple devices to use the same Internet connection.
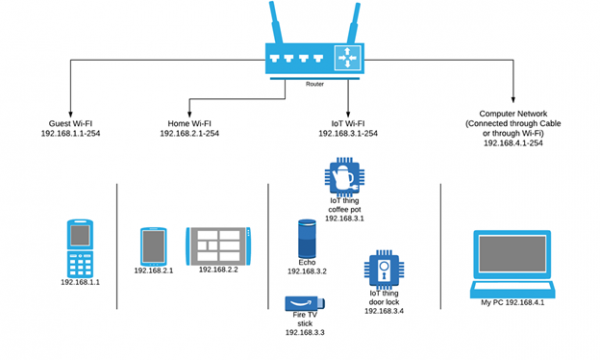
There are several types of routers, but most routers pass data between LANs (local area networks) and WANs (wide area networks).
A LAN is a group of connected devices restricted to a specific geographic area. A LAN usually requires a single router.
A WAN, by contrast, is a large network spread out over a vast geographic area. Large organizations and companies that operate in multiple locations across the country, for instance, will need separate LANs for each location, which then connects to the other LANs to form a WAN. Because a WAN is distributed over a large area, it often necessitates multiple routers and switches.
GATEWAY:
While a router is used to join two similar types of networks, a gateway is used to join two dissimilar networks. Dissimilar could be used to describe networks that use different primary protocols.
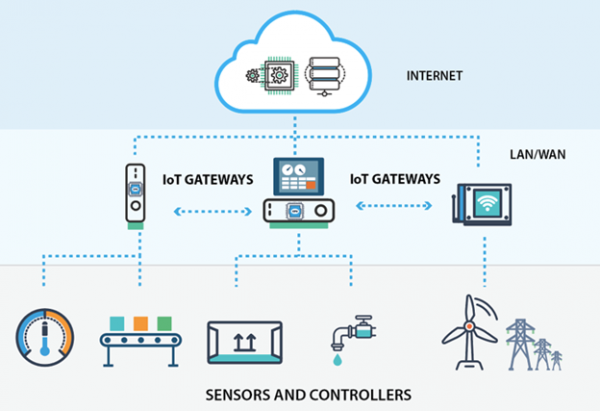
A gateway is a hardware device that goes about as a "gate" between two networks. It very well might be a server, firewall, router, or another device that empowers traffic to stream all through the network. Gateways serve as an exit and entry point for a network as all data should go through or communication gateway before being routed. In most IP-based networks, the only traffic that does not go through at least one gateway is traffic flowing among nodes on the same local area network (LAN) segment.
SUBNET:
A subnet, or subnetwork, is a segmented piece of a larger network. More specifically, subnets are a logical partition of an IP network into multiple, smaller network segments. The practice of dividing a network into two or more networks is called subnetting.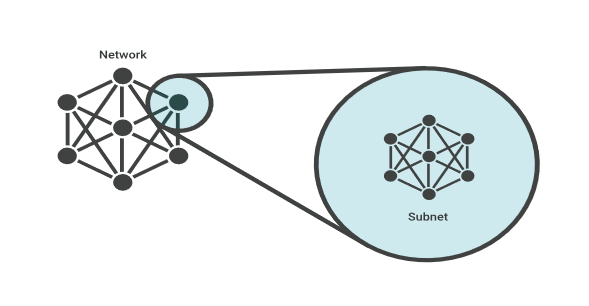
Each subnet allows its connected devices to communicate with each other, while routers are used to communicate between subnets.
Subnet Mask:
When you connect a device to a network, the network assigns an IP address to the device. That IP address consists of two parts: the network portion and the host portion. The network portion of the IP address identifies the overall network while the host portion identifies the device. A subnet mask is a number that distinguishes the network address and the host address within an IP address.
.png)
FIREWALL:
A Firewall is a network security device that monitors, and filters (accepts, rejects, or drops) incoming and outgoing network traffic based on an organization's previously established security policies.
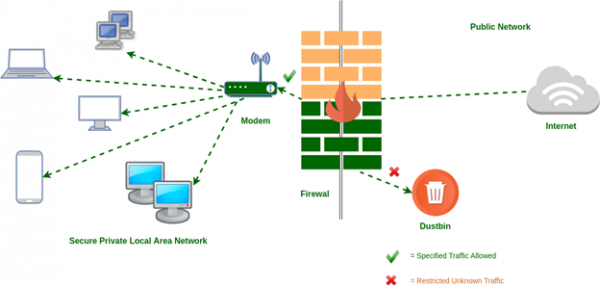
At its most basic, a firewall is essentially the barrier that sits between a private internal network and the public Internet. A firewall's main purpose is to allow non-threatening traffic in and to keep dangerous traffic out.
History and Need for Firewall: Before Firewalls, network security was performed by Access Control Lists (ACLs) residing on routers. ACLs are ruled that determine whether network access should be granted or denied to a specific IP address.
But ACLs cannot determine the nature of the packet it is blocking. Also, ACL alone does not have the capacity to keep threats out of the network. Hence, the Firewall was introduced.
DEMILITARIZED ZONE:
In computer security, a DMZ network (sometimes referred to as a "demilitarized zone") functions as a subnetwork containing an organization's exposed, outward-facing services. It acts as the exposed point to an untrusted network, commonly the Internet.
The goal of a DMZ is to add an extra layer of security to an organization's local area network. A protected and monitored network node that faces outside the internal network can access what is exposed in the DMZ, while the rest of the organization's network is safe behind a firewall.
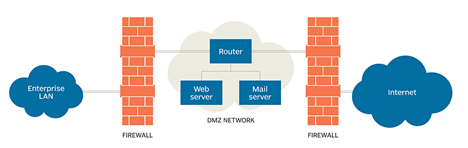
When implemented properly, a DMZ Network gives organizations extra protection in detecting and mitigating security breaches before they reach the internal network, where valuable assets are stored.
Purpose of a DMZ:
The DMZ Network exists to protect the hosts most vulnerable to attack. These hosts usually involve services that extend to users outside of the local area network, the most common examples being email, web servers, and DNS servers. Because of the increased potential for attack, they are placed into the monitored subnetwork to help protect the rest of the network if they become compromised.
Hosts in the DMZ have tightly controlled access permissions to other services within the internal network because the data passed through the DMZ is not as secure. On top of that, communications between hosts in the DMZ and the external network are also restricted to help increase the protected border zone. This allows hosts in the protected network to interact with the internal and external network, while the firewall separates and manages all traffic shared between the DMZ and the internal network. Typically, an additional firewall will be responsible for protecting the DMZ from exposure to everything on the external network.
All services accessible to users on communicating from an external network can and should be placed in the DMZ if one is used. The most common services are:
• Web Servers
• Mail Servers
• FTP Servers
Blog Disclaimer: The opinions expressed within these blog posts are solely the author’s and do not reflect the opinions and beliefs of the Certitrek, CWNP or its affiliates.



